DMARC allows you to resist phishing - fraud, the purpose of which is to steal confidential user data (logins, passwords, credit card information). The main phishing tool is email letters. Typically, attackers disguise their messages as messages from well-known companies using their domains. If the user follows the instructions from such a letter, he loses personal data and often money. And the company suffers significant reputational damage.
If the company has DMARC configured, then the email sent by scammers on its behalf will either not be delivered at all or will be marked as suspicious.

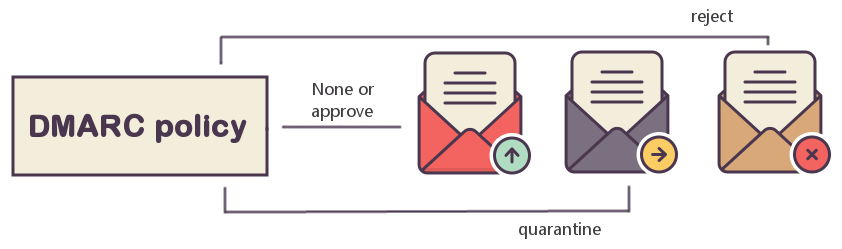
DMARC is a protocol that tells the server what to do with the message if the DKIM and SPF records are incorrect. Correct DKIM and SPF confirm that the email was sent from the domain specified in the "From:" field in the email.
Thus, DMARC, along with SPF and DKIM, is responsible for mail authentication. That is, for the sender authentication procedure.
Let's see how these records differ.
DKIM works like this: the letter contains encrypted data about who and when the letter was sent. The mail provider receives this data along with the letter. The provider decrypts them using the public key posted on the domain from which the letter was sent. If the data matches, then this is an honest sender, and the letter can be skipped to the Inbox. If not, it is a scammer, the letter goes to Spam.
SPF indicates whether a particular server is allowed to send emails from that domain. The server is identified by its IP address. For example, when you send a Campaign using a cold mailing service or set up corporate mail, you delegate the provider's and service's servers the right to send emails from your domain. SPF detects a trusted sender by IP
Now let's deal with DMARC. This entry:
tells the mail provider what to do with the message depending on the results of reading DKIM and SPF;
tells the server to send a report to the mail of the domain administrator (that is, you or your system administrator) with information about what letters were sent and how the provider dealt with the letters.